Archive for April 2014
Basic Terminal Commands For Linux
In this tutorial you will learn to use linux terminal. You will learn to navigate on theterminal, learn to create and remove file and much more. Most of this commands also works on Mac Os X and powershell on windows.
What Is Terminal ?
Basically you are reading this tutorial because you are new to linux or want to learn using terminal to navigate. Before you get started you must have linux installed or running virtually on your computer. I would recommend downloading fedora or ubuntu (If you have trouble installing ubuntu leave a comment below and i will post a tutorial).Commands To Remember
This are some of commands you must remember which will help you to use terminal more easily.ls - it will list all files and folder in your current directory
ls -l it will give detailt listing of all files and folders
ls -a it will list all files and folder in your current directory including hidden files (files and folders that begin with period)
pwd will print your working directory or simply your current directory
Navigating In Terminal
Here i may refer folder as directory so dont get confused. This is the term we use in linux for folders.cd - cd stands for change directory. we use cd follow by path address to navigate ro that folder.
Eg: cd Desktop will make desktop as my current directory.
cd / will make root as you current directory
cd ~ will make home as your current directory
Typing cd alone is same as cd ~ and it will make home as your current directory
cd .. will make parent directory i.e directory above your current directory
cd ../../ will take you two folder up
Creating Files And Folder
mkdir - we use mkdir follow by path or folder name to create a directoryEg mkdir car will create directory car in your current directory
to create folder recursively i.e folder inside folder inside folder we use -p flag
Eg mkdir -p vehicles/car/truck will create directory vehicles in your current directory which have car inside it and car has directory truck in it.
touch - we use touch follow by file name to create empty file.
Removing Files And Folders
rmdir - we use rmdir follow by path to to remove any directory. This will not work if folder you are trying to remove has something in it.rm -r to remove file recursively which can not be removed by rmdir
rm - We use this command to remove files
Posted by Unknown
Tag :
linux
Websites To Learn Computer Programming Languages

1. W3schools.com
If you are a beginner or intermediate programmer, then w3schools is an excellent website for learning programming. W3schools offer tutorials for a variety of web programming and scripting languages such as html, html5, css, asp, Ajax, JavaScript, php, jQuery etc. So, if you are into web development then w3schools would be a great learning resource.
2. Codeavengers.com:
If you want learn coding for making games, apps or websites using html/html5, css3, JavaScript python, but want an entertaining teaching resource. Then codeavengers.com is ideal choice for you. Codeavengers.com was designed by keeping difficulty for beginners in mind. It provides a fun and interactive learning environment that is effective for all age groups. Even if you are an intermediate programmer, you might find some great learning stuff there.


3. Codecademy.com
Codecademy is another great website, for learning languages like JavaScript, HTML/CSS, PHP, Python, and Ruby. You can even learn how to use some popular web APIs in your website or app. Codecademy has a great modern learning system, which is based on user interaction. It has full-fledged programming courses for beginners. Again, this website is great for beginners and intermediate learners. But advanced programmers can also find some pretty useful stuff there.


4. tutorialspoint.com
Tutorialspoint has tutorials for a lot of web, high level and scripting languages that are commonly used today. You can find tutorials for any computer language that you have ever heard of (those that are currently in used). Apart from that, it also features a variety of tutorials for other fields such as DIP, OS, SEO, Telecom, DBMS, and frameworks etc. Some commonly used languages that you can learn there are: Java, C++, PHP, Python, Ruby, C#, Perl, VB.Net, ios.


5. msdn.microsoft.com
Although, beginner programmers might find MSDN (Microsoft Developer Network) a tough learning resource, it is still the best resource you can get, if you want to master Microsoft oriented languages such as VB.Net, C# etc. MSDN has great tutorials for beginners, intermediate and advance programmers.

But as I stated earlier, beginners might not be initially comfortable with MDSN, as I has really a lot of resources that it would be a hard time for beginners to find what they are looking for. But if you get used to MSDN, then it is the ideal learning point for Microsoft oriented languages. You can get a lot of sample applications, tutorials and resources that are uploaded by Microsoft and MSDN community. Since it’s a developer’s network, you can even find development help from community members.
6. Lynda.com
You might already know about Lynda.com. Lynda offers easy to follow video tutorials. Lynda.com is an old and well established tutoring site, if you are looking for video tutorials to learn computer languages, then Lynda is your ideal choice. Apart from programming languages, Lynda also offers tutorials for a variety of other fields such as 3D modeling, CAD, Photography etc. Lynda.com is an old and well established tutoring site.


So the next time someone asks you about your computer skills, you know where to turn. I hope you will learn a lot from these websites. All the best :)
Posted by Unknown
Tag :
internet tricks
Keyloggers And How To Be Safe From Keyloggers
In this tutorial i am going to talk about the most use piece of software besides from RAT by hackers to observe your activities on your computer and that is keyloggers. A keylogger is a software or hardware device which monitors each and every key typed by you on your keyboard. I am going to talk about different types of keylogger and how to be safe from keyloggers. So lets learn something about keyloggers.
1. What is keylogger ?
You might have heard about keyloggers but really dont know what they are reading this article will clear your mind. A keylogger also know as keystroke logger is software or hardware device which monitors each and every key typed by you on your keyboard. You can not identify the presence of keylogger on your computer since it runs in background and also it is not listed in task manager or control panel. It can be used by parents to keep eye on their childrens or company owner to spy on their employes.2. How it can harm you ?
In this section i will talk about how keylogger can harm you in different ways for example It can be used by your enemy or friend to get sensitive information such as your username and password, Bank credit card details, or any other activities you do on your computer.
- Example: You login in to your Facebook account from a computer in which keylogger is install then your username and password will be captured.
3. Types of keyloggers
There are two types of keylogger hardware keylogger and software keylogger. Software keylogger is install in your computer where as a Hardware keylogger is attached to your keyboard. Looking at below images will clear your mind.
HARDWARE KEYLOGGER

SOFTWARE KEYLOGGER

4. How to Protect yourself from keyloggers ?
Keylogger can be used by your enemy to get sensitive information such as your Bank credit card details, or password of any social networking sites etc. In order to be safe keep following points in your mind.
- Never use your online banking from cyber cafe. If you want to use then you can try this method. open notepad and type anything Then copy and paste each word that comes in your username or password.
- You can even use above method to protect your facebook profile, yahoo or gmail id.
- When you enter cyber cafe make sure that no hardware device is attached to keyboard wire. Its look something similar to above image.
Posted by Unknown
Tag :
windows tricks
6 Most Common Password Cracking Methods And Their Countermeasures
There are number of methods out their used by hackers to hack your account or get your personal information. Today in this post i will share with you guys 6 Most commonly used method to crack password and their countermeasures. You must check out this article to be safe and to prevent your online accounts from hacking.
1. Brute Force Attack
Any password can be cracked using Brute-force attack. Brute-force attacks try every possible combinations of numbers, letters and special characters until the right password is match. Brute-force attacks can take very long time depending upon the complexity of the password. The cracking time is determined by the speed of computer and complexity of the password.
Countermeasure: Use long and complex passwords. Try to use combination of upper and lowercase letters along with numbers. Brute-force attack will take hundreds or even thousands of years to crack such complex and long passwords.
Example: Passwords like "iloveu" or "password" can be cracked easily whereas computer will take years to crack passwords like "aN34lL00"
2. Social Engineering
Social engineering is process of manipulating someone to trust you and get information from them. For example, if the hacker was trying to get the password of a co-workers or friends computer, he could call him pretending to be from the IT department and simply ask for his login details. Sometime hackers call the victim pretending to be from bank and ask for their credit cards details. Social Engineering can be used to get someone password, to get bank credentials or any personal information.
Countermeasure: If someone tries to get your personal or bank details ask them few questions. Make sure the person calling you is legit. Never ever give your credit card details on phone.
3. Rats And Keyloggers
In keylogging or RATing the hacker sends keylogger or rat to the victim. This allows hacker to monitor every thing victim do on his computer. Every keystroke is logged including passwords. Moreever hacker can even control the victims computer.
Countermeasure: Never login to your bank account from cyber cafe or someone else computer. If its important use on-screen or virtual keyboard while tying the login. Use latest anti-virus software and keep them updated. Check out below article to know more about Rats and Keyloggers.
4. Phishing
Phishing is the most easiest and popular hacking method used by hackers to get someone account details. In Phishing attack hacker send fake page of real website like facebook, gmail to victim. When someone login through that fake page his details is send to the hacker. This fake pages can be easily created and hosted on free web-hosting sites.
Countermeasure: Phishing attacks are very easy to avoid. The url of this phishing pages are different from the real one. For example URL of phishing page of facebook might look like facbbook.com (As you can see There are two "b"). Always make sure that websites url is correct. Check out below article to know more about phishing.
5. Rainbow Table
A Rainbow table is a huge precomputed list of hashes for every possible combination of characters. A password hash is a password that has gone through a mathematical algorithm such as md5 and is transformed into something which is not recognizable. A hash is a one way encryption so once a password is hashed there is no way to get the original string from the hashed string. A very commonly used hashing algorithm to store passwords in website databases is MD5. It is almost similar to dictionary attack, the only difference is, in rainbow tables attack hashed characters are used as passwords whereas in dictionary attack normal characters are used as passwords.
Example: ‘hello’ in md5 is 5d41402abc4b2a76b9719d911017c592 and zero length string ("") is d41d8cd98f00b204e9800998ecf8427e
Countermeasure: Make sure you choose password that is long and complex. Creating tables for long and complex password takes a very long time and a lot of resources
6. Guessing
This seems silly but this can easily help you to get someones password within seconds. If hacker knows you, he can use information he knows about you to guess your password. Hacker can also use combination of Social Engineering and Guessing to acquire your password.
Countermeasure: Don't use your name, surname, phone number or birthdate as your password. Try to avoid creating password that relates to you. Create complex and long password with combination of letters and numbers.
Posted by Unknown
Tag :
windows tricks
What Is Phishing And How To Be Safe From Phishing ?
Phishing is one of the type of hacking . It is a method of acquiring sensitive information such as username, password, bank information etc. Phishing page could be said as an duplicate page of real one. Its look exactly similar as the real page.But when user enter sensitive information on such phishing page his information is send to the E-mail address provided in the phishing page or you can say the one who created that phishing page. Phishing page is mostly send via mail. Target of phishing are mostly social networking sites like facebook, orkut etc. Also Banks website to acquire credit card details,website like yahoo, gmail are also target of phishing.
Example of Phishing scams:
- Email asking you to login to your locked account to unlock it.
- Email carrying a Link to sites like Facebook,yahoo etc and asking you to Login.
- Emails containing some Information of your Interest and asking you to Login to Your Account.
How to be safe from phishing ?
- Never login to any of your account through link provided in the Email.
- Go to real website don't click on any link posted anywhere. such as link posted on your facebook wall by friend or link provided in comments or link to certain website on any blog.
- Check the URL of website before entering any sensitive information. Because the URL of phishing page is not same as the URL of real one.
- Real gmail page looks like gmail.com while phishing looks different somthing likegmail.anything.com
Posted by Unknown
Tag :
linux
Remove All Your Google Web History

In this post, I'll show you how to remove your entire Google web history.
Before we begin, please note that any data you remove will be deleted permanently. Google keeps a lot of useful information that helps you find what you're looking for faster. It gives you quick access to webpages you've visited in the past, and even lets you know in search results which pages you've visited, and when. This information can be useful if you're a power user, and like to get things done quickly.
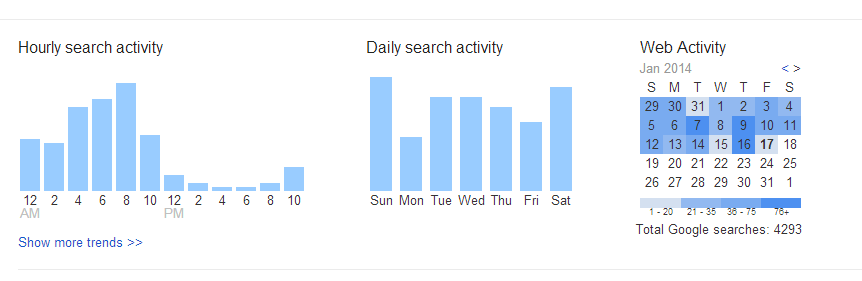
But if you still want, you can go ahead and erase your entire web history. You can also pick and choose individual items to remove, so that you won't lose everything.
Delete your Google Web History
Follow these steps to partially or completely.- Step 1: Visit your Google History page at https://www.google.com/history. Alternatively, you can click the gear icon
on the upper right corner of a search results page, and then go to Search history.
- Step 2: Click on the gear
icon again, and then go to Settings.
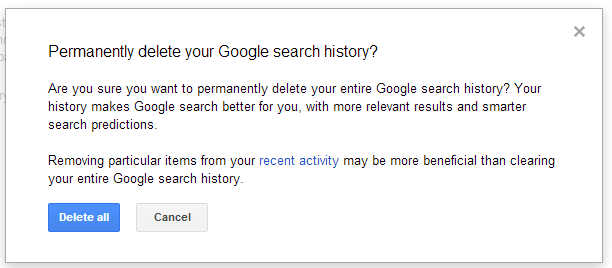
- Step 3: Click on the delete all link. You'll be prompted for a confirmation. Click on Delete all again, and your entire search history is gone!
- Step 4 (optional): Click on the Turn off button on the Settings page to stop Google from storing your history again
If you don't want to delete your entire history, you can select individual items from the History main page, and delete them. This, by no means, implies that Google has nothing more to do with your data. They still keep some of your information on their servers for auditing and other such purposes. But at least your personal data is off the line now, and isn't susceptible to leaking out into the wrong hands.
Posted by Unknown
Tag :
internet tricks
Hide Files Behind The Images

There are some important files or document you want to hide from others on your computer. To do that you might be creating folder inside folder to hide such files but in today's tutorial i will change this by teaching you a interesting trick to hide files behind images.To hide a file behind a image means that if any one opens that image he will see the image, but to see the hidden file we need to open that image in a specific way. So let's get started.
How To Hide File Behind Image ?
In order to do this you should have basic understanding of command line.
1. Select an image to be used for hiding file behind the image.
2. Now select a file to hide behind the image and make it in .RAR format. With the help of the WinRAR.
3. And most important is that paste both the files on desktop. You may do this anywhere instead of desktop if you have some basic understanding of command line.
4. Now open cmd by going to Start > Accessories > Command Prompt and type following commands in it.
cd desktop
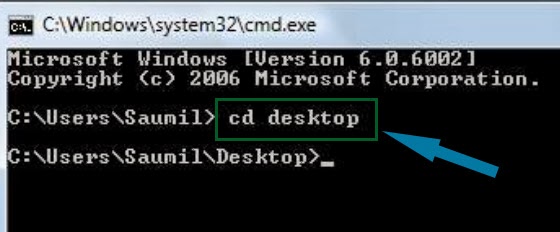
5. CD stands for change directory by typing above command you change your directory to desktop. After that type command given below.
Copy /b imagename.jpg + filename.rar finalimage.jpg
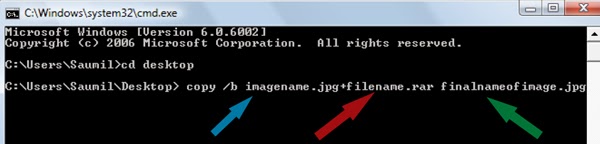
- Replace imagename.jpg with the name of image you want your file to be hidden behind. Don't forget to add image format (Eg: .jpg,.png,.gif)
- Replace filename with name of your file you want to hide. It must be in .rar format.
- Finally Replace finalimage.jpg with whatever name you want your final image with hidden files should be. This is the image where your file will be hidden.
6. Now when you will try to open this newly created image it will open as normal image, but to open you hidden file you need follow steps given below.
How To Access Hidden File ?
To access your hidden file you need to open the newly created image in winrar. Just follow simple steps given below to do that.
1. Open winrar
2. Now locate your image and open it or simply drag your image in winrar.
3. Extract the file and done.
Posted by Unknown
Tag :
windows tricks
Best Call Recorder for iPhone to Record Conversations
So even though you can record all incoming and outgoing calls on your iPhone? I think NO! As from years and years, no one has ever cam across such application to record your calls. It has been a major problem for the users who wanted to record calls on their iPhone. But today i will tell you how to record calls on your iPhone so easily with an application.
iPhone call recorder is currently supported only by jail broken devices and is not supported by non-jailbreak devices. So to get this call recorder on your iPhone just follow the simple steps given below.
How to install it?
Open cydia on your device and add this repo in your packages.
repo.insanelyi.com
After adding up with the repo, now search for the Audio Recorder and install it.
Your iPhone will be rebooted once, after completing the process, go to-
Settings>Audio Recorder

Now turn it ON. Now its in enabled mode. Check the settings you need to do as per your requirement. Basic settings include-
Record Calls – ALL
Beep Sound- OFF
You have just activated the call recorded now whenever you receive a call or outgoing call you make, calls will be automatically recorded.
How to see recorded calls?
Whenever you do a call or receive a call, you will notice a red icon blinking on your screen, which means the calls are being recorded.
After completing your call, when you hang up, you will see a badge alert on your icon of call recorder as shown below. This indicates you have a new call recording in your iPhone.
Now tap to open it and see the recording listen it or you can also forward it via mail.
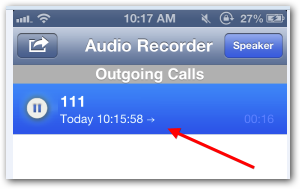
This application allows you to record calls incoming or outgoing. Disabling beep indicates that the caller on the other end wont be able to know wether the call is being recorded or not. Doing such act without the knowledge of other is against laws. So kindly do it at your own risk.
Posted by Unknown
Tag :
iphone
jailbreak iDevice running iOS 7 using evasi0n7 [Windows]
Finally the long awaited jailbreak tool for the iOS 7 has arrived. It is a joyful moments for the iDevices users, as now they are free from the jailed devices and can do anything tricky with their devices. The best thing of this tool is that it is compatible with all the subversion of iOS 7 i.e. 7.0.1, 7.0.2, 7.0.3 and iOS 7.0.4
As in the past the evad3rs team released a friendly UI tool, this time too the tool is easy to use and has been named as evasi0n7 which allows a user to jailbreak device running iOS 7.

The tool is easy to use still we have this Windows guide to help you out to carry out the jailbreak process easily without any problem.
Thing to Note- This jailbreak tool only works with iPhone, iPad, iPad mini and iPod Touch devices which are running on the iOS 7.0 via iOS 7.0.4. So kindly note that it wont work on Apple TV or any of apple devices which are running on iOS version < iOS 7. Please make sure to backup your device before proceeding. Or should have backup in iCloud or iTunes. For the users who have done Over the Air (OTA) update, make sure to backup your device to iTunes and follow for full restore before proceeding with the jailbreak7.
Tools Required: evasi0n7 (Download now)
Step 1: Open the download file, Extract it and open the evasion file.
Step 2: Before proceeding, kindly check your device passcode lock has been disabled.
Step 3: Connect your iDevice using USB to your computer.
Step 4: The jailbreak tool will automatically detect your iDevice and display its information. The dull Jailbreak button will now be activated to proceed further.
Step 5: Now to begin further for the jailbreaking, click the Jailbreak button and don't do anything either with the device nor with computer till it needs some action.
Step 6: After sometime, the tool window will ask you to tap the evasi0n7 icon which is on your home screen. Open the device, tap on it to complete the process.
Step 7: Meanwhile your device will reboot and display black screen. Not to worry, the jailbreak process is being processed.
Step 8: After the process gets done, your device will be turned on. Now, tap to open your device home screen, a Cydia icon will be present there. And there you go!
This whole process will be completed within 5-10 minutes. If your device gets stuck at any step during the process, kindly reboot it and restart with all the steps. If it is stuck in between then you can restart it by holding down both power and home button simultaneously to reboot it forcefully.
If you have any problems, or any other query regarding the process then kindly use our comment section. Happy Jailbreaking!
Posted by Unknown
Add Folders and Software to My Computer in Windows7,8.
My Computer is most useful feature in Windows OS. My computer allows you to access your drives and devices connected to you PC

Because,Computer is most useful service in Windows OS so you might want to your favorite in Computer. Computer is not a regular folder so you can’t just drop a shortcut there the usual way. But there is a quick way to get a shortcut listed in Computer and here’s how.
Follow these Steps to add Folder in Computer.
- First pres in "Windows + R" and then paste this %appdata% in the box and Press Enter Key. This will open a hidden folder “Roaming”.
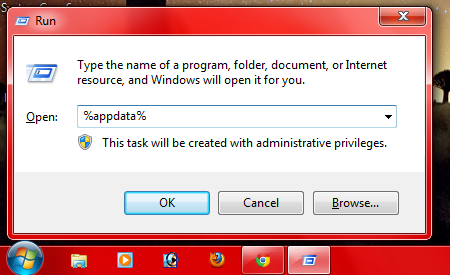
- Now paste bellow code in the link bar of Windows Explorer and Enter Key.
\Microsoft\Windows\Network Shortcuts
- Now Network Shortcuts folder will open. Here you can paste the shortcuts of the folder and software which you want to add in My Computer.
- Now just close Network Shortcuts folder and see in you Computer.
Posted by Unknown
Tag :
windows tricks
Categories
Blog Archive
-
2014
(79)
- August (1)
- June (5)
- May (20)
-
April
(43)
- Basic Terminal Commands For Linux
- Websites To Learn Computer Programming Languages
- Keyloggers And How To Be Safe From Keyloggers
- 6 Most Common Password Cracking Methods And Their ...
- What Is Phishing And How To Be Safe From Phishing ?
- Remove All Your Google Web History
- Hide Files Behind The Images
- Best Call Recorder for iPhone to Record Conversations
- jailbreak iDevice running iOS 7 using evasi0n7 [Wi...
- Add Folders and Software to My Computer in Windows...
- Make any Window transparent using a keyboard Short...
- Get Taskbar transparency in Windows 8
- View India in 360 with WoNoBo.com or with there An...
- How to Block Ads on Android Apps, Games and Browser’s
- Retrieve Your Wireless Network Security Key in Win...
- Use Alternate DNS Servers In Windows For Faster In...
- Use The Google Chrome Flash Plugin in Firefox in U...
- Encrypt Your Flash Drives In Ubuntu Linux Using Di...
- Use Google Chrome As The Default PDF Viewer In Ubuntu
- Change the GNOME Keyring Password For Easier Autom...
- Add a New Default Search Engine To Google Chrome W...
- Change the Default LightDM Background Image In Ubuntu
- Turn Off The Startup Sound In Windows Vista and Wi...
- Find, View and Analyze BSOD Dump Files
- Disable Aero (Permanently or Temporarily) in Windo...
- Change the Windows 7 Login Image without Editing t...
- Getting Started With Google Drive For Windows
- Use Google Web Fonts in the Google Docs Word Proce...
- Merge Two Partitions in Windows
- Change Where Chrome Downloads Files To
- View Photo EXIF Metadata on iPhone, Mac, and Windows
- Track Your iPhone, iPad, and Mac Computer
- Remove Duplicate Contacts on iPhone
- Create a Multiple Operating System Bootable USB Drive
- Guide to Taking Screenshots in Windows 8
- 99 Ways to Make Your Computer Fast
- Tips to Avoid Installing Browser Extensions with A...
- Some methods to Make Sure No One is Monitoring You...
- Get back the corrupted files in pendrive without a...
- Download YouTube videos using VLC media player wit...
- HIDE A FOLDER IN NOKIA PHONE WITHOUT ANY SOFTWARE
- Some Common Internet Error Codes With Meanings
- CCleaner is Now Available for Android
- March (10)


.jpg)









